JWT assertion's Signature with RS256 algorithm
I'm using Box.com for my ColdFusion application. For creating JWT assertion we need 3 parts(as mentioned in the document).
So as per this document, they've given the steps to create HEADER and CLAIMS, but not about how to create SIGNATURE. I've also browsed in external sources, all sources have been made with HS256 algorithms. But Box.com API supports only “RS256″, “RS384″, and “RS512″ algorithms.
So I'm strucked here in, how to create SIGNATURE part with RS256 algorithms. Any help would be appreciated.
-
The signature is generated as part of the token signing process. You feed your payload, private key, public key, and options to a library that will do the signing for you and generate the JWT token. (it will look as you have described
..). You don't have to construct the signature portion on your own. The library will generate this for you. I haven't done this in Cold Fusion, but in JavaScript on Node.js I used a library called "jswebtoken" that can be installed via npm. Looking at the Cold Fusion code in the blog post below, the code is very similar to the little sample I got running.
I did a quick Google search for Cold Fusion and JWT and ran across this blog posting:
The author has a a small library for Cold Fusion to enable encoding and decoding of JWT tokens and he has recently added support for RSA support (including RS256 which can be used with the Box API).
I hope this helps get you started.
Thanks,
John -
I'm in agreement with Rajeshal, the documentation for assertion Signature appears incomplete. I was able to create the Header and Claim, but stuck at signature. Then to make it even more of a challenge, i've been requested to complete this with PowerShell. I've searched the internet for days, tried jwt.io amoung other things but it seems i'm either getting that wrong or its just not compatible.
Could you guys box just not complete the documentation and provide a full example? Or even provide a token creation tool? When looking through forum's it appears many people are struggling with this. Please keep all terminology inline with your documenation. Claim, Header and Signature. - The documenation doesn't descibe PAYLOAD. Nor does it describe any requirements to use a library. I'm not a full time developer but in general, i can work my way through guides but not when they appear incomplete. Step 1 through to 6 made perfect sense, i got kudos from my progress.. But step 7 doesn't make sense "Required String The JWT Assertion mentioned above". It doesn't follow step 6.. Please provide a comprehensive guide, with all the json and detailed examples. Or maybe even a video to compliment.
-
I'm stuck in a similar situation in Swift. It looks like I can encode public and private keys separately with the SwiftyRSA library.
My problem is that I can't somehow put them together the way the JWT assertion wants it for Box. I've read through plenty of documentation, but I'm having trouble trying to do that.
Would anyone be willing to look at this and tell me the one or two steps I'm missing? This is the hardest API I've ever worked with lol
Thanks in advance!
-
My purpose was a little different, I was just trying to make a JWT assertion on Postman, but ran into the same issue of how to format the Signature part of the assertion. So I know nothing about coldfusion or powershell, but hope this helps:
On this page: https://developer.box.com/guides/authentication/jwt/without-sdk/
It says this: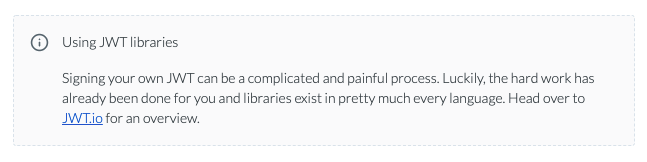 So when you go to the JWT.io that Box recommended, click on debugger https://jwt.io/#debugger-io, choose your algorithm:
So when you go to the JWT.io that Box recommended, click on debugger https://jwt.io/#debugger-io, choose your algorithm: 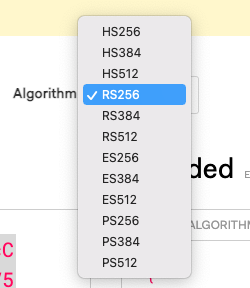
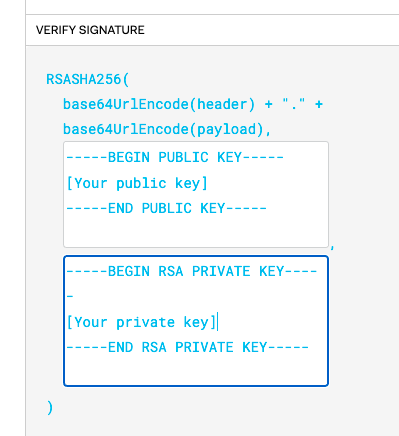
Then put your Box public key and private key in the corresponding boxes:
Your public key is in your Box Developers Console --> [Your Box App] --> Configuration tab. Scroll Down to:
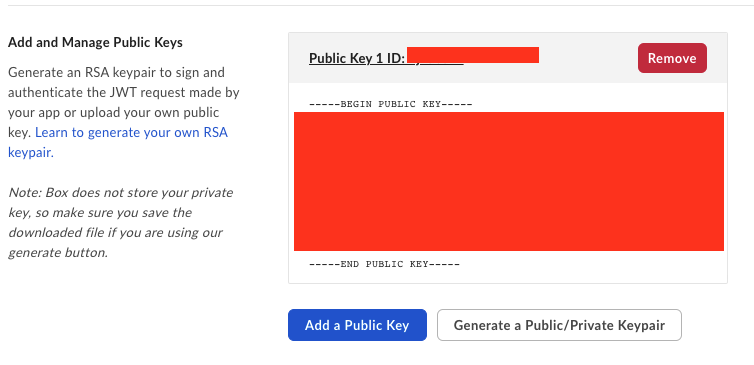
Copy that Public Key. Your private key is your private key decrypted. (I was able to manually decrypt it through terminal on mac, and with openssl): https://how2itsec.blogspot.com/2020/01/use-openssl-to-decrypt-private-key.html
After pasting it in, make sure it says "Signature Verified" on the bottom:

And then after that, the api endpoint worked and I was able to get an access token, so I'm assuming the format of the signature was correct.
投稿コメントは受け付けていません。
コメント
5件のコメント